AWS Landing Zone is a solution that helps customers more quickly set up a secure, multi-account AWS environment based on AWS best practices. With the large number of design choices, setting up a multi-account environment can take a significant amount of time, involve the configuration of multiple accounts and services, and require a deep understanding of AWS services.
It can help save time by automating the set-up of an environment for running secure and scalable workloads while implementing an initial security baseline through the creation of core accounts and resources. It also provides a baseline environment to get started with a multi-account architecture, identity and access management, governance, data security, network design, and logging.
- Based on AWS best practices and recommendations
- Initial security and governance controls
- Baseline accounts and account vending machine
- Automated deployment
- A configured, secure, scalable, multi-account AWS environment based on AWS best practices
- A starting point for net new development and experimentation
- A starting point for customers’ application migration journey
- An environment that allow for iteration and extension over time
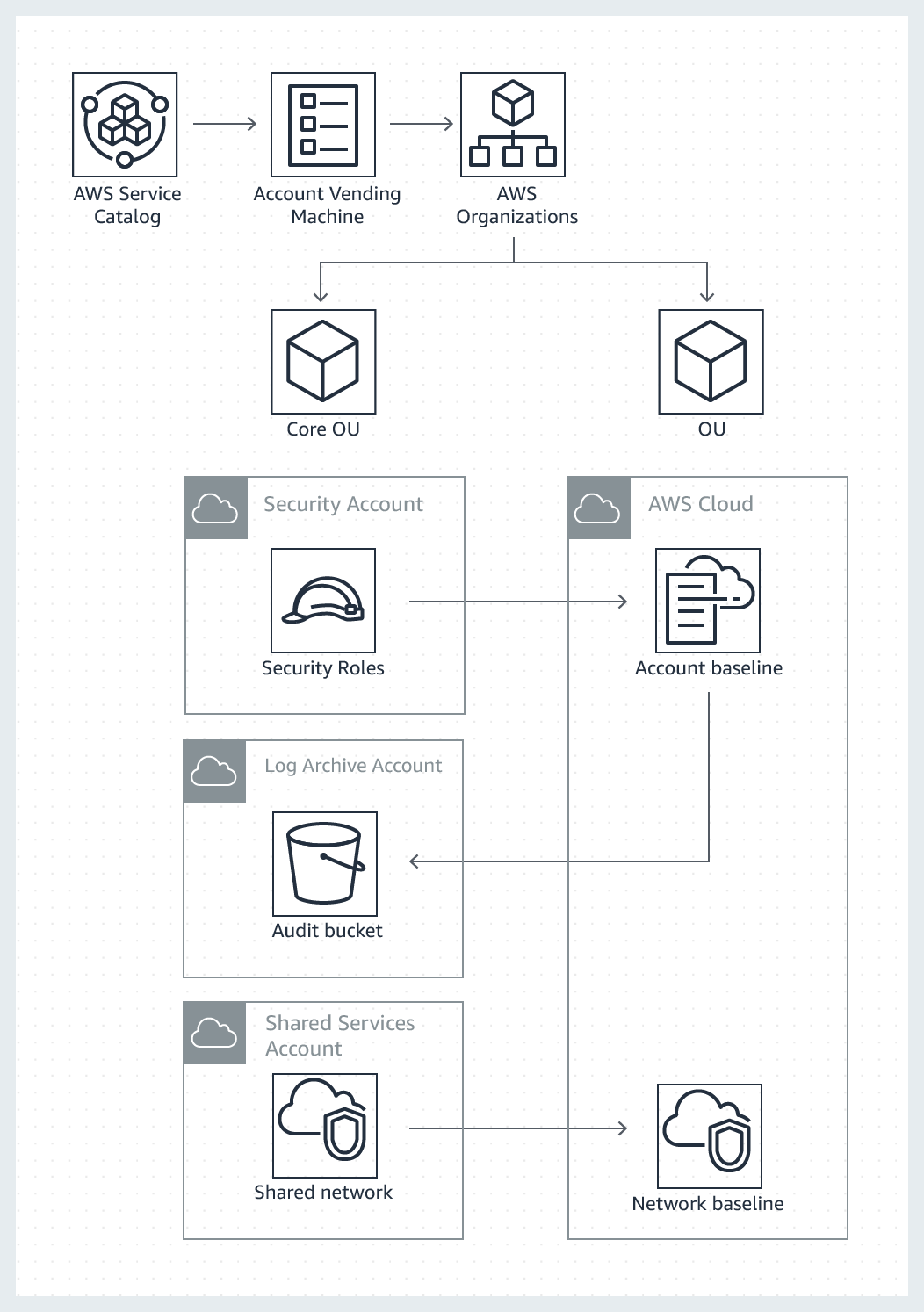
The AWS Landing Zone solution deploys an AWS Account Vending Machine (AVM) product for provisioning and automatically configuring new accounts. The AVM leverages AWS Single Sign-On (SSO) for managing user account access. This environment is customizable to allow customers to implement their own account baselines through a Landing Zone configuration and update pipeline.
The AWS Landing Zone solution includes four accounts, and add-on products that can be deployed using the AWS Service Catalog such as the Centralized Logging solution and AWS Managed AD and Directory Connector for AWS SSO.
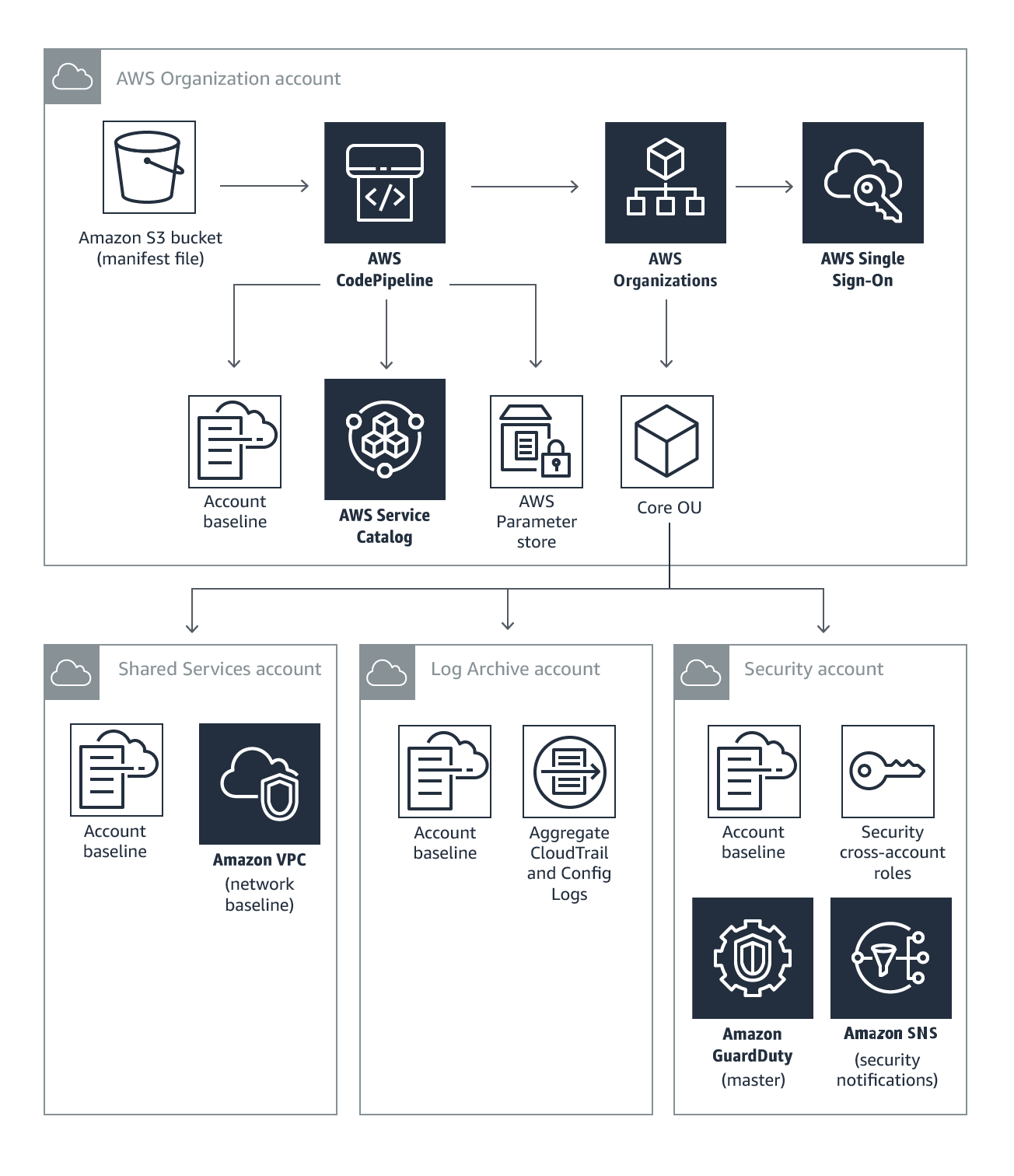
The AWS Landing Zone is deployed into an AWS Organizations account. This account is used to manage configuration and access to AWS Landing Zone managed accounts. The AWS Organizations account provides the ability to create and financially manage member accounts. It contains the AWS Landing Zone configuration Amazon Simple Storage Service (Amazon S3) bucket and pipeline, account configuration StackSets, AWS Organizations Service Control Policies (SCPs), and AWS Single Sign-On (SSO) configuration.
The Shared Services account is a reference for creating infrastructure shared services such as directory services. By default, this account hosts AWS Managed Active Directory for AWS SSO integration in a shared Amazon Virtual Private Cloud (Amazon VPC) that can be automatically peered with new AWS accounts created with the Account Vending Machine (AVM).
The Log Archive account contains a central Amazon S3 bucket for storing copies of all AWS CloudTrail and AWS Config log files in a log archive account.
The Security account creates auditor (read-only) and administrator (full-access) cross-account roles from a Security account to all AWS Landing Zone managed accounts. The intent of these roles is to be used by a company's security and compliance team to audit or perform emergency security operations in case of an incident.
This account is also designated as the master Amazon GuardDuty account. Users from the master account can configure GuardDuty as well as view and manage GuardDuty findings for their own account and all of their member accounts.
The Account Vending Machine (AVM) is an AWS Landing Zone key component. The AVM is provided as an AWS Service Catalog product, which allows customers to create new AWS accounts in Organizational Units (OUs) preconfigured with an account security baseline, and a predefined network.
AWS Landing Zone leverages AWS Service Catalog to grant administrators permissions to create and manage AWS Landing Zone products and end user’s permissions to launch and manage AVM products.
The AVM uses launch constraints to allow end users to create new accounts without requiring account administrator permissions.
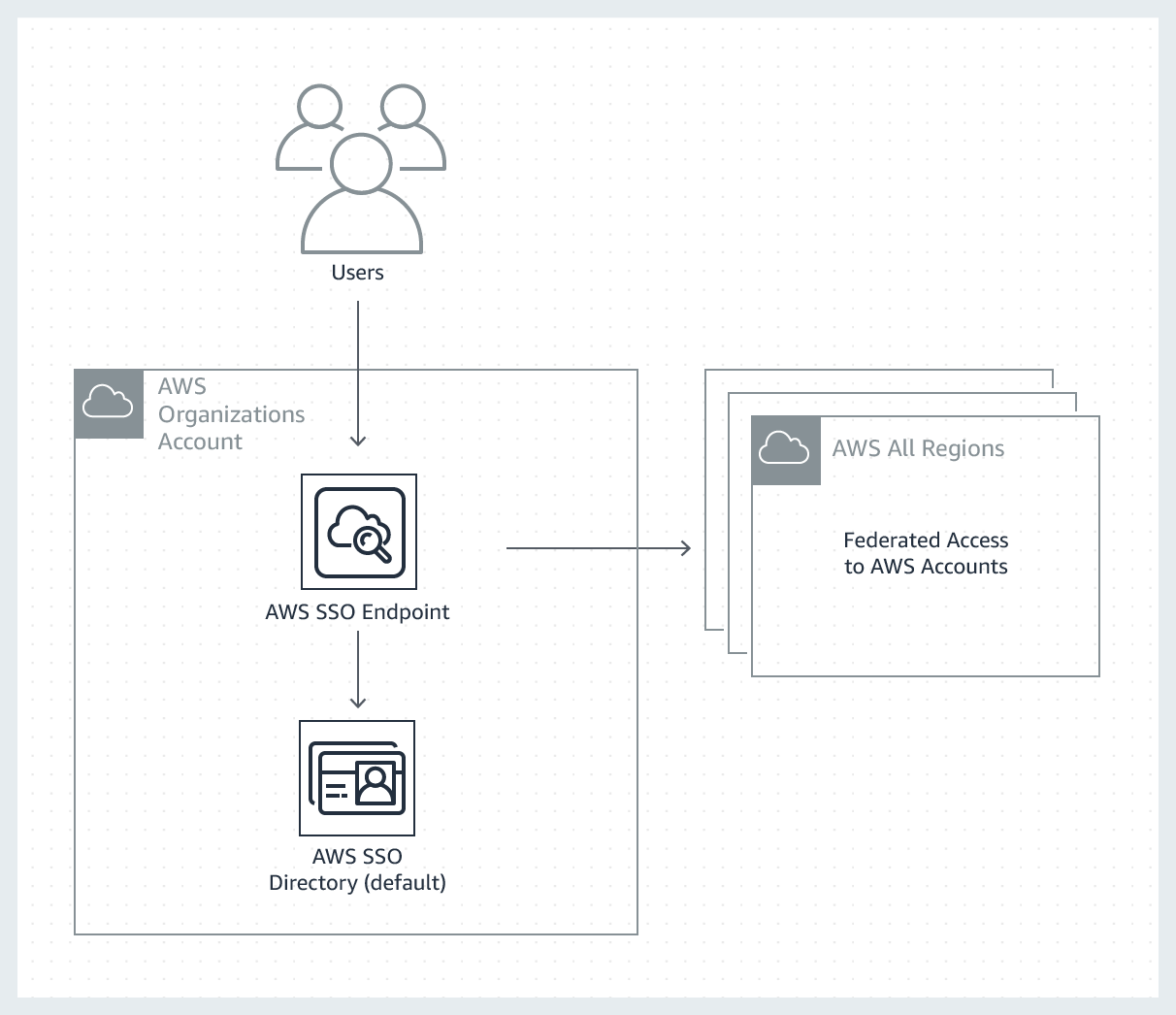
Providing least-privilege, individual user access to your AWS accounts is an essential, foundational component to AWS account management. The AWS Landing Zone solution provides customers two options to store their users and groups.
The default configuration deploys AWS Single Sign-On (SSO) with AWS SSO directory where users and groups can be managed in SSO.
A single-sign-on endpoint is created to federate user access to AWS accounts.
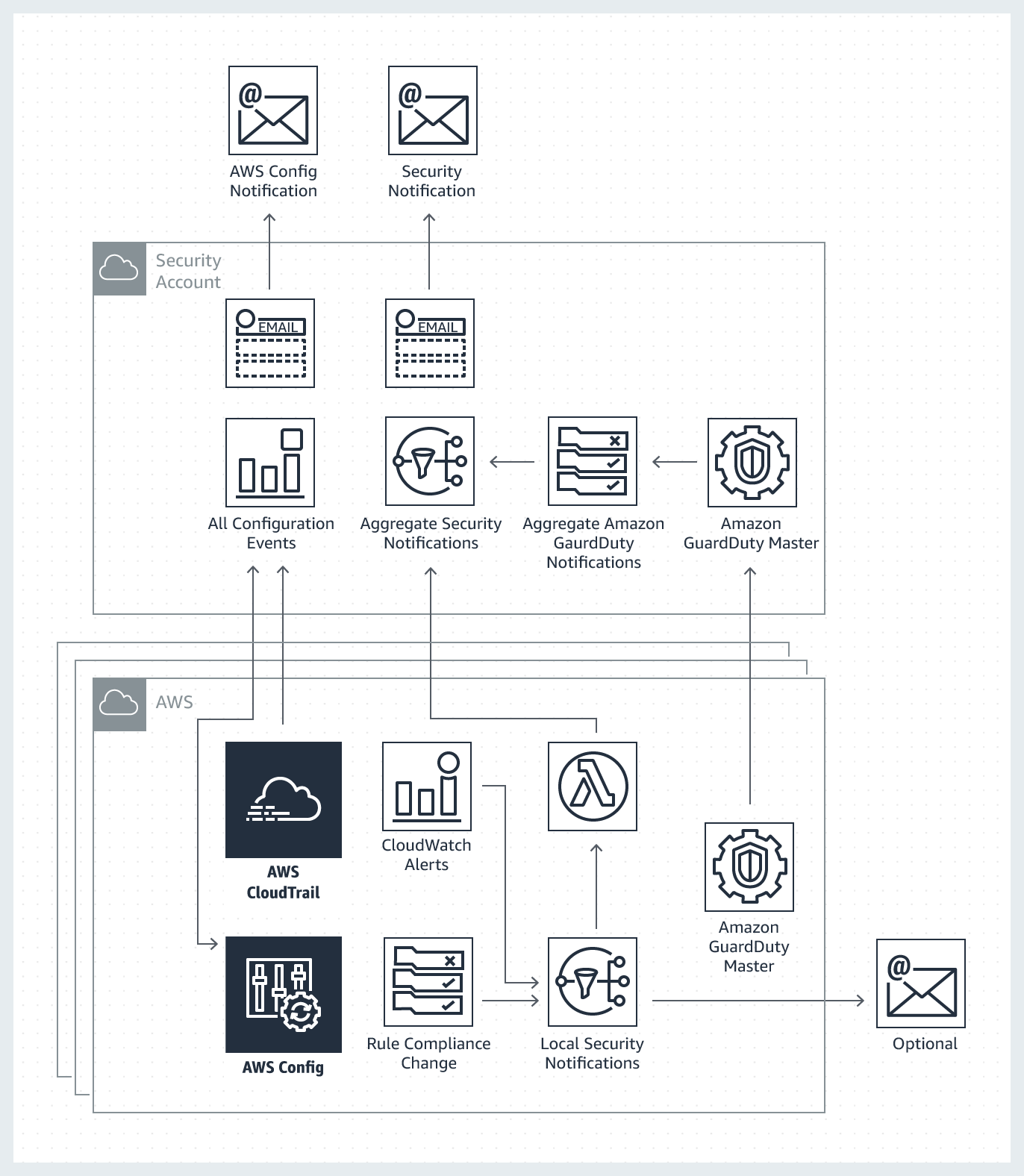
The AWS Landing Zone solution configures Amazon CloudWatch alarms and events to send a notification on root account login, console sign-in failures, API authentication failures, and the following changes within an account: security groups, network ACLs, Amazon VPC gateways, peering connections, ClassicLink, Amazon Elastic Compute Cloud (Amazon EC2) instance state, large Amazon EC2 instance state, AWS CloudTrail, AWS Identity and Access Management (IAM) policies, and AWS Config rule compliance status.
The solution configures each account to send notifications to a local Amazon Simple Notification Service (Amazon SNS) topic.
The All Configuration Events topic aggregates AWS CloudTrail and AWS Config notications from all managed accounts.
The Aggregate Security Notifications topic aggregates security notifications from specific Amazon CloudWatch events, AWS Config Rules compliance status change events, and AWS GuardDuty findings.
An AWS Lambda function is automatically subscribed to the security notifications topic to forward all notifications to an aggregation Amazon SNS topic in the AWS Organizations account.
This architecture is designed to allow local administrators to subscribe to and receive specific account notifications.
The AWS Service Catalog Portfolio has add-on feature that allow customers to extend their Landing Zone implementation by dropping in the add-on Micro-configuration into their existing Landing Zone Configuration. The default implementation creates the AWS Service Catalog Portfolio AWS Landing Zone - Add-On Products and deploys add-on products.
This add-on deploys AWS Microsoft Active Directory (Microsoft AD) to provide AWS Single Sign-On (AWS SSO) access to your user directory. By default, Microsoft AD is deployed into the Shared Services account to separate AD user management from AWS Landing Zone management functions. This makes it easier to leverage AD for applications or operating system management.
This add-on deploys AWS Elasticsearch cluster hosted in shared service account and deploys a Lambda functions to collect CloudTrail, VPC Flow logs and CloudWatch logs from all accounts to be stored and indexed in AWS Elasticsearch service.
The AWS Landing Zone is out-of-box solutions designed and developed by AWS architects. It powers by many different AWS services behind the scene. Not easy to adopt for beginners.
- Additional layer of abstraction on top of it to make your life easy.
- Provide single location for implementation and management of Landing Zone
- Extend “Landing Zone” by adding more features and add-on products.
- Transit VPC integration
- Additional Security Guardrail checks
- Ability to Share AMI/Snapshot
- Golden AMI creation process
- Create new and/or extend your current CICD process in Landing Zone
- Help you to customize it based on your need.
- Help you to make a decision and design multi-account architecture
- Train your team and bring them on next level.
Create an account
Prerequisites
Setup Wizard (1-8 steps) (How your landing zone should look like)
Landing Zone implementation (monitor status of implementation)
Landing Zone deployment (monitor status of deployment)
Launch AVM (Add new accounts to your landing zone)
Success (View and monitor your AWS Organization from our tool)